>For communication and synchronization
–Shared memory
–OS provided IPC
>Message system
–no need for shared variable
– two operations
•send(message) – message size fixed or variable
•receive(message)
>If P and Q wish to communicate, they need to
–establish a communication link between them
–exchange messages via send/receive
>Implementation of communication link
–physical (e.g., shared memory, hardware bus)
–logical (e.g., logical properties)
.....MAHAL KITA PERO MAS MAHAL KO ANG SARILI KO!!!
Thursday, July 16, 2009
4.) COOPERATING PROCESSES
>Advantages of process cooperation
–Information sharing
–Computation speed-up
–Modularity
–Convenience
>Independent process cannot affect/be affected by the execution of another process, cooperating ones can
>Issues
–Communication
–Avoid processes getting into each other’s way
–Ensure proper sequencing when there are dependencies
>Common paradigm: producer-consumer
–unbounded-buffer - no practical limit on the size of the buffer
–bounded-buffer - assumes fixed buffer size
–Information sharing
–Computation speed-up
–Modularity
–Convenience
>Independent process cannot affect/be affected by the execution of another process, cooperating ones can
>Issues
–Communication
–Avoid processes getting into each other’s way
–Ensure proper sequencing when there are dependencies
>Common paradigm: producer-consumer
–unbounded-buffer - no practical limit on the size of the buffer
–bounded-buffer - assumes fixed buffer size
3.) OPERATION PROCESS
A.) PROCESS ON CREATION
Parent process creates children processes, which, in turn create other processes, forming a tree of processes.
Resource sharing:
>Parent and children share all resources.
>Children share subset of parent’s resources.
>Parent and child share no resources.
Execution:
>Parent and children execute concurrently.
>Parent waits until children terminate.
B.) PROCESS TERMINATION
>Process executes last statement and asks the operating system to delete it (exit).
>Output data from child to parent (via wait).
>Process’ resources are deallocated by operating system.
>Parent may terminate execution of children processes (abort).
>Child has exceeded allocated resources.
>Task assigned to child is no longer required.
>Parent is exiting.
>Operating system does not allow child to continue if its parent terminates.
>Cascading termination.
>In Unix, if parent exits children are assigned init as parent
Parent process creates children processes, which, in turn create other processes, forming a tree of processes.
Resource sharing:
>Parent and children share all resources.
>Children share subset of parent’s resources.
>Parent and child share no resources.
Execution:
>Parent and children execute concurrently.
>Parent waits until children terminate.
B.) PROCESS TERMINATION
>Process executes last statement and asks the operating system to delete it (exit).
>Output data from child to parent (via wait).
>Process’ resources are deallocated by operating system.
>Parent may terminate execution of children processes (abort).
>Child has exceeded allocated resources.
>Task assigned to child is no longer required.
>Parent is exiting.
>Operating system does not allow child to continue if its parent terminates.
>Cascading termination.
>In Unix, if parent exits children are assigned init as parent
2.) PROCESS SHEDULING
A.) SCHEDULING QUEUSE
>Job queue – set of all processes in the system.
>Ready queue – set of all processes residing in main memory, ready and waiting to >Execute.Device queues – set of processes waiting for an I/O device.
>Processes migrate between the various queues.
B.) SCHEDULERS
>Long-term scheduler (or job scheduler) – selects which processes should be brought into the ready queue.
>Short-term scheduler (or CPU scheduler) – selects which process should be executed next and allocates CPU.
>Short-term scheduler is invoked very frequently (milliseconds) fi (must be fast).
>Long-term scheduler is invoked very infrequently (seconds, minutes) fi (may be slow).
>The long-term scheduler controls the degree of multiprogramming.
>Processes can be described as either:
>I/O-bound process – spends more time doing I/O than computations, many short CPU bursts.
>CPU-bound process – spends more time doing computations; few very long CPU bursts.
C.) CONTEXT SWITCH
>When CPU switches to another process, the system must save the state of the old process and load the saved state for the new process.
>Context-switch time is overhead; the system does no useful work while switching.
>Time dependent on hardware support.
>Job queue – set of all processes in the system.
>Ready queue – set of all processes residing in main memory, ready and waiting to >Execute.Device queues – set of processes waiting for an I/O device.
>Processes migrate between the various queues.
B.) SCHEDULERS
>Long-term scheduler (or job scheduler) – selects which processes should be brought into the ready queue.
>Short-term scheduler (or CPU scheduler) – selects which process should be executed next and allocates CPU.
>Short-term scheduler is invoked very frequently (milliseconds) fi (must be fast).
>Long-term scheduler is invoked very infrequently (seconds, minutes) fi (may be slow).
>The long-term scheduler controls the degree of multiprogramming.
>Processes can be described as either:
>I/O-bound process – spends more time doing I/O than computations, many short CPU bursts.
>CPU-bound process – spends more time doing computations; few very long CPU bursts.
C.) CONTEXT SWITCH
>When CPU switches to another process, the system must save the state of the old process and load the saved state for the new process.
>Context-switch time is overhead; the system does no useful work while switching.
>Time dependent on hardware support.
1.) THE CONCEPTS OF PROCESS
A.) PROCESS STATE
-As a process executes, it changes state
new: The process is being created.F running: Instructions are being executed.
waiting: The process is waiting for some event to occur.
ready: The process is waiting to be assigned to a processor
terminated: The process has finished execution.
B.) PROCESS CONTROL BLACK
-Information associated with each process.
>Process ID
>Process state
>Program countern CPU registers
>CPU scheduling information
>Memory-management information
>Accounting information
>I/O status information
C.) THREADS
-Each process provides the resources needed to execute a program. A process has a virtual address space, executable code, open handles to system objects, a security context, a unique process identifier, environment variables, a priority class, minimum and maximum working set sizes, and at least one thread of execution. Each process is started with a single thread, often called the primary thread, but can create additional threads from any of its threads.
-As a process executes, it changes state
new: The process is being created.F running: Instructions are being executed.
waiting: The process is waiting for some event to occur.
ready: The process is waiting to be assigned to a processor
terminated: The process has finished execution.
B.) PROCESS CONTROL BLACK
-Information associated with each process.
>Process ID
>Process state
>Program countern CPU registers
>CPU scheduling information
>Memory-management information
>Accounting information
>I/O status information
C.) THREADS
-Each process provides the resources needed to execute a program. A process has a virtual address space, executable code, open handles to system objects, a security context, a unique process identifier, environment variables, a priority class, minimum and maximum working set sizes, and at least one thread of execution. Each process is started with a single thread, often called the primary thread, but can create additional threads from any of its threads.
Thursday, July 9, 2009
QUIZ NUMBER 3
1.) WHAT ARE THE MAJOR ACTIVITIES OF THE O.S WITH REGARDS TO PROCESS MANAGEMENT.
- Process creation and deletion
- Process suspension and resumption
- Provision of management for:
- Process synchornization
- Process communication
- Deadlack handling
2.) WHAT ARE THE MAJOR ACTIVITIES OF THE O.S WITH REGARDS TO MEMORY MANAGEMENT.
- Keep track of w/ parts of memory are curently being used and by whom.
- Decide w/c porcess to load when memory space becomes avalable.
- Allocate and dellocate memory space as needed.
3.) WHAT ARE THE MAJOR ACTIVITIES OF THE O.S WITH REGARDS TO SECONDARY-STORAGE MANAGEMENT.
- Free space management.
- Storage allocation.
- Disk scheduling.
4.) WHAT ARE THE MAJOR ACTIVITIES OF THE O.S WITH REGARDS TO FILE MANAGEMENT.
- File creation and deletion.
- Directory creation and deletion.
- Support of primitives for manipulating files and directories.
- Mapping files onto secondary storage.
- File backup on stable (volatile) storage media.
5.) WHAT IS THE PURPOSE OF THE COMMAND INTERPRETER
- Serves as the interface between the user and the operating system.
- User friendly, mouse based windows environment in the macintosh and in microsoft windows.
- Many command are given to the operating system by control statement with deals.
- Program that read and interpreters control statements is called variously.
Tuesday, July 7, 2009
SYSTEM BOOT
Operating system must be made available to hardware so hardware can start it
Small piece of code – bootstrap loader, locates the kernel, loads it into memory, and starts it
Sometimes two-step process where boot block at fixed location loads bootstrap loader
When power initialized on system, execution starts at a fixed memory location
Firmware used to hold initial boot code
Small piece of code – bootstrap loader, locates the kernel, loads it into memory, and starts it
Sometimes two-step process where boot block at fixed location loads bootstrap loader
When power initialized on system, execution starts at a fixed memory location
Firmware used to hold initial boot code
VIRTUAL MACHINE
• A virtual machine takes the layered approach to its logicalconclusion. It treats hardware and the operating system kerneas though they were all hardware.
• A virtual machine provides an interface identical to theunderlying bare hardware.
• The operating system creates the illusion of multipleprocesses, each executing on its own processor with its own(virtual) memory.
• The resources of the physical computer are shared to createthe virtual machines.
– CPU scheduling can create the appearance that usershave their own processor.
– Spooling and a file system can provide virtual card readeand virtual line printers.
– A normal user time-sharing terminal serves as the virtualmachine operator’s console.
IMPLEMENTATION OF VIRTUAL MACHINE
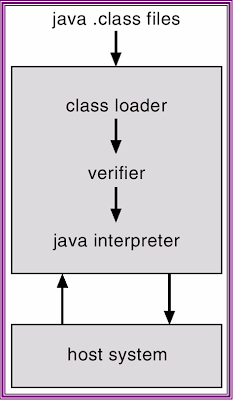
-Interpretation of Java bytecode results in slow execution of program.First version of Java Virtual Machine(JVM) implementation was relied on interpretation techniques. On the other hand performance can be improved by translating the Java bytecode into machine code by a Just-In-Time(JIT) compiler and this technique is being integrated into most JVM implementations. Java is an automatic garbage collected language, freeing the programmer from the explicit memory management. Garbage collection "pause" time can be reduced by using a generational garbage collection. This thesis describes an implementation of a JVM. The specific contributions made in this thesis include: development of a Just-In-Time(JIT) compiler using DAG construction technique, a bytecode interpreter, a generational garbage collector. Our implementation can execute Java bytecode either by an interpreter or the bytecode can be translated into machine code using the JIT compiler and the translated code is directly executed by the processor. We have implemented the Java Native Interface (JNI) to enable using C and assembly language programs with Java.
BENEFITS OF VIRTUAL MACHINE
-Virtual machines have been around for a long time but they really have not become common place in many development shops. It is unfortunate since virtual machines provide so many benefits to developers and testers alike. This article will discuss some of the benefits of virtual machines and review two of the most popular virtual machine software packages available for Windows.
EXAMPLE OF VIRTUAL MACHINE
-
• A virtual machine provides an interface identical to theunderlying bare hardware.
• The operating system creates the illusion of multipleprocesses, each executing on its own processor with its own(virtual) memory.
• The resources of the physical computer are shared to createthe virtual machines.
– CPU scheduling can create the appearance that usershave their own processor.
– Spooling and a file system can provide virtual card readeand virtual line printers.
– A normal user time-sharing terminal serves as the virtualmachine operator’s console.
IMPLEMENTATION OF VIRTUAL MACHINE
-Interpretation of Java bytecode results in slow execution of program.First version of Java Virtual Machine(JVM) implementation was relied on interpretation techniques. On the other hand performance can be improved by translating the Java bytecode into machine code by a Just-In-Time(JIT) compiler and this technique is being integrated into most JVM implementations. Java is an automatic garbage collected language, freeing the programmer from the explicit memory management. Garbage collection "pause" time can be reduced by using a generational garbage collection. This thesis describes an implementation of a JVM. The specific contributions made in this thesis include: development of a Just-In-Time(JIT) compiler using DAG construction technique, a bytecode interpreter, a generational garbage collector. Our implementation can execute Java bytecode either by an interpreter or the bytecode can be translated into machine code using the JIT compiler and the translated code is directly executed by the processor. We have implemented the Java Native Interface (JNI) to enable using C and assembly language programs with Java.
BENEFITS OF VIRTUAL MACHINE
-Virtual machines have been around for a long time but they really have not become common place in many development shops. It is unfortunate since virtual machines provide so many benefits to developers and testers alike. This article will discuss some of the benefits of virtual machines and review two of the most popular virtual machine software packages available for Windows.
EXAMPLE OF VIRTUAL MACHINE
-

SYSTEM GENARATION (SYSGEN)
> Operating systems are designed to run on any of a class of machines; the system must be configured for each specific computer siten SYSGEN program obtains information concerning the specific configuration of the hardware systemn Booting
– starting a computer by loading the kerneln Bootstrap program
– code stored in ROM that is able to locate the kernel, load it into memory, and start its execution
– starting a computer by loading the kerneln Bootstrap program
– code stored in ROM that is able to locate the kernel, load it into memory, and start its execution
Saturday, July 4, 2009
4.) SYSTEM STRUCTURE
Simple Structure
>View the OS as a series of levels>Each level performs a related subset of functions
>Each level relies on the next lower level to perform more primitive functions
>This decomposes a problem into a number of more manageable subproblems
Layered Approach
The operating system is divided into a number of layers (levels), each built on top of lower layers. The bottom layer (layer 0), is the hardware; the highest (layer N) is the user interface.
Thursday, July 2, 2009
1.) SYSTEM COMPONENT
OPERATING SYSTEM PROCESS MANAGEMENT
-A process is a program in execution. A process needs certain resources: CPU time, memory (address space), files, and I/O devices, to accomplish its task.
The operating system is responsible for the following activities in connection with process management.
>Process creation and deletion.
>Process suspension and resumption.
>Provision of mechanisms for:
>Process synchronization
>Process communication
MAIN MEMORY MANAGEMENT
-Memory is a large array of words or bytes, each with its own address. It is a repository of instructions and data shared by the CPU and I/O devices. Main memory is a volatile storage device. It loses its contents in the case of system failure.
The operating system is responsible for the following activities in connections with memory management:
>Decide which processes to load when memory space becomes available.
>Allocate and deallocate memory space as needed. Keep track of which parts of memory are currently being used and by whom.
FILE MANAGEMENT
-A file is a collection of related information defined by its creator. Commonly, files represent programs (both source and object forms) and data.
The operating system is responsible for the following activities in connections with file management:
>File creation and deletion.
>Directory creation and deletion.
>Support of primitives for manipulating files and directories.
>Mapping files onto secondary storage.
>File backup on stable (nonvolatile) storage media.
>Files on floppy are inaccessible
>Ffiles on floppy are part of file hierarchy
I/O SYSTEM MANAGEMENT
-The I/O system consists of:
>A buffer-caching system
>A general device-driver interface
>Drivers for specific hardware devices
SECONDARY STORAGE MANAGEMENT
-Since main memory (primary storage) is volatile and too small to accommodate all data and programs permanently, the computer system must provide secondary storage to back up main memory.
Most modern computer systems use disks as the principle on-line storage medium, for both programs and data.
The operating system is responsible for the following activities in connection with disk management:
-->Free space management
-->Storage allocation
-->Disk scheduling
PROTETION SYSTEM
-Protection refers to a mechanism for controlling access by programs, processes, or users to both system and user resources.
The protection mechanism must:
>Distinguish between authorized and unauthorized usage.
>Specify the controls to be imposed.
>Provide a means of enforcement.
COMMAND-INTERPRETER
-Command-Interpreter reads commands from the user or from a file of commandsand executes them, usually by turning them into one or more systemcalls. It is usually not part of the kernel since the command interpreteris subject to changes.
The program that reads and interprets control statements is called variously:
>command-line interpreter
>shell (in UNIX)Its function is to get and execute the next command statement
-A process is a program in execution. A process needs certain resources: CPU time, memory (address space), files, and I/O devices, to accomplish its task.
The operating system is responsible for the following activities in connection with process management.
>Process creation and deletion.
>Process suspension and resumption.
>Provision of mechanisms for:
>Process synchronization
>Process communication
MAIN MEMORY MANAGEMENT
-Memory is a large array of words or bytes, each with its own address. It is a repository of instructions and data shared by the CPU and I/O devices. Main memory is a volatile storage device. It loses its contents in the case of system failure.
The operating system is responsible for the following activities in connections with memory management:
>Decide which processes to load when memory space becomes available.
>Allocate and deallocate memory space as needed. Keep track of which parts of memory are currently being used and by whom.
FILE MANAGEMENT
-A file is a collection of related information defined by its creator. Commonly, files represent programs (both source and object forms) and data.
The operating system is responsible for the following activities in connections with file management:
>File creation and deletion.
>Directory creation and deletion.
>Support of primitives for manipulating files and directories.
>Mapping files onto secondary storage.
>File backup on stable (nonvolatile) storage media.
>Files on floppy are inaccessible
>Ffiles on floppy are part of file hierarchy
I/O SYSTEM MANAGEMENT
-The I/O system consists of:
>A buffer-caching system
>A general device-driver interface
>Drivers for specific hardware devices
SECONDARY STORAGE MANAGEMENT
-Since main memory (primary storage) is volatile and too small to accommodate all data and programs permanently, the computer system must provide secondary storage to back up main memory.
Most modern computer systems use disks as the principle on-line storage medium, for both programs and data.
The operating system is responsible for the following activities in connection with disk management:
-->Free space management
-->Storage allocation
-->Disk scheduling
PROTETION SYSTEM
-Protection refers to a mechanism for controlling access by programs, processes, or users to both system and user resources.
The protection mechanism must:
>Distinguish between authorized and unauthorized usage.
>Specify the controls to be imposed.
>Provide a means of enforcement.
COMMAND-INTERPRETER
-Command-Interpreter reads commands from the user or from a file of commandsand executes them, usually by turning them into one or more systemcalls. It is usually not part of the kernel since the command interpreteris subject to changes.
The program that reads and interprets control statements is called variously:
>command-line interpreter
>shell (in UNIX)Its function is to get and execute the next command statement
3.) SYSTEM CALLS
- An operating system (O/S) is a program with two jobs: it manages the resources of the computer (peripherals, files, memory, etc.) and it manages all other programs running on the computer.
PROCESS CONTROL
-Process control is a statistics and engineering discipline that deals with architectures, mechanisms, and algorithms for controlling the output of a specific process. See also control theory.
For example, heating up the temperature in a room is a process that has the specific, desired outcome to reach and maintain a defined temperature (e.g. 20°C), kept constant over time. Here, the temperature is the controlled variable. At the same time, it is the input variable since it is measured by a thermometer and used to decide whether to heat or not to heat. The desired temperature (20°C) is the setpoint. The state of the heater (e.g. the setting of the valve allowing hot water to flow through it) is called the manipulated variable since it is subject to control actions.
A commonly used control device called a programmable logic controller, or a PLC, is used to read a set of digital and analog inputs, apply a set of logic statements, and generate a set of analog and digital outputs. Using the example in the previous paragraph, the room temperature would be an input to the PLC. The logical statements would compare the setpoint to the input temperature and determine whether more or less heating was necessary to keep the temperature constant. A PLC output would then either open or close the hot water valve, an incremental amount, depending on whether more or less hot water was needed. Larger more complex systems can be controlled by a Distributed Control System (DCS) or SCADA system.
FILE MANAGEMENT
-The term computer file management refers to the manipulation of [document]s and [data] in [Computer filefile]s on a [computer]].
Specifically, one may create a new file or edit an existing file and save it; open or load a pre-existing file into memory; or close a file without saving it. Additionally, one may group related files in directories. These tasks are accomplished in different ways in different operating systems and depend on the user interface design and, to some extent, the storage medium being used.
DEVICE MANAGEMENT
-Device Management is a set of technologies, protocols and standards used to allow the remote management of mobile devices, often involving updates of firmware over the air (FOTA). The network operator, handset OEM or in some cases even the end-user (usually via a web portal) can use Device Management, also known as Mobile Device Management, or MDM, to update the handset firmware/OS, install applications and fix bugs, all over the air. Thus, large numbers of devices can be managed with single commands and the end-user is freed from the requirement to take the phone to a shop or service center to refresh or update.
For companies, a Device Management system means better control and safety as well as increased efficiency, decreasing the possibility for device downtime. As the number of smart devices increases in many companies today, there is a demand for managing, controlling and updating these devices in an effective way. As mobile devices have become true computers over the years, they also force organizations to manage them properly. Without proper management and security policies, mobile devices pose threat to security: they contain lots of information, while they may easily get into wrong hands. Normally an employee would need to visit the IT / Telecom department in order to do an update on the device. With a Device Management system, that is no longer the issue. Updates can easily be done "over the air". The content on a lost or stolen device can also easily be removed by "wipe" operations. In that way sensitive documents on a lost or a stolen device do not arrive in the hands of others.
INFORMATION MAINTENANCE
-A one or two-year program open to juniors and seniors who want to work with the repair and maintenance of computers OR the networking of computers. Repair and maintenance: This class will prepare students with competencies essential for repairing and maintaining computer hardware and operating systems, as well as simple network concepts. Qualified students may enroll in coursework that may lead to certification as an A+ Computer Technician. Networking: Second year students may enroll in Cisco Academy or sample the high tech areas of computer usage that include internet concepts and applications and computer hardware and electronic interfacing projects. Qualified students may enroll in coursework that may lead to a Cisco Certified Network Associate (CCNA) or Network+ Certification.
PROCESS CONTROL
-Process control is a statistics and engineering discipline that deals with architectures, mechanisms, and algorithms for controlling the output of a specific process. See also control theory.
For example, heating up the temperature in a room is a process that has the specific, desired outcome to reach and maintain a defined temperature (e.g. 20°C), kept constant over time. Here, the temperature is the controlled variable. At the same time, it is the input variable since it is measured by a thermometer and used to decide whether to heat or not to heat. The desired temperature (20°C) is the setpoint. The state of the heater (e.g. the setting of the valve allowing hot water to flow through it) is called the manipulated variable since it is subject to control actions.
A commonly used control device called a programmable logic controller, or a PLC, is used to read a set of digital and analog inputs, apply a set of logic statements, and generate a set of analog and digital outputs. Using the example in the previous paragraph, the room temperature would be an input to the PLC. The logical statements would compare the setpoint to the input temperature and determine whether more or less heating was necessary to keep the temperature constant. A PLC output would then either open or close the hot water valve, an incremental amount, depending on whether more or less hot water was needed. Larger more complex systems can be controlled by a Distributed Control System (DCS) or SCADA system.
FILE MANAGEMENT
-The term computer file management refers to the manipulation of [document]s and [data] in [Computer filefile]s on a [computer]].
Specifically, one may create a new file or edit an existing file and save it; open or load a pre-existing file into memory; or close a file without saving it. Additionally, one may group related files in directories. These tasks are accomplished in different ways in different operating systems and depend on the user interface design and, to some extent, the storage medium being used.
DEVICE MANAGEMENT
-Device Management is a set of technologies, protocols and standards used to allow the remote management of mobile devices, often involving updates of firmware over the air (FOTA). The network operator, handset OEM or in some cases even the end-user (usually via a web portal) can use Device Management, also known as Mobile Device Management, or MDM, to update the handset firmware/OS, install applications and fix bugs, all over the air. Thus, large numbers of devices can be managed with single commands and the end-user is freed from the requirement to take the phone to a shop or service center to refresh or update.
For companies, a Device Management system means better control and safety as well as increased efficiency, decreasing the possibility for device downtime. As the number of smart devices increases in many companies today, there is a demand for managing, controlling and updating these devices in an effective way. As mobile devices have become true computers over the years, they also force organizations to manage them properly. Without proper management and security policies, mobile devices pose threat to security: they contain lots of information, while they may easily get into wrong hands. Normally an employee would need to visit the IT / Telecom department in order to do an update on the device. With a Device Management system, that is no longer the issue. Updates can easily be done "over the air". The content on a lost or stolen device can also easily be removed by "wipe" operations. In that way sensitive documents on a lost or a stolen device do not arrive in the hands of others.
INFORMATION MAINTENANCE
-A one or two-year program open to juniors and seniors who want to work with the repair and maintenance of computers OR the networking of computers. Repair and maintenance: This class will prepare students with competencies essential for repairing and maintaining computer hardware and operating systems, as well as simple network concepts. Qualified students may enroll in coursework that may lead to certification as an A+ Computer Technician. Networking: Second year students may enroll in Cisco Academy or sample the high tech areas of computer usage that include internet concepts and applications and computer hardware and electronic interfacing projects. Qualified students may enroll in coursework that may lead to a Cisco Certified Network Associate (CCNA) or Network+ Certification.
2.) OPERATING SYSTEM SERVICES
-An operating system (commonly abbreviated to either OS or O/S) is an interface between hardware and user; an OS is responsible for the management and coordination of activities and the sharing of the resources of the computer. The operating system acts as a host for computing applications that are run on the machine. As a host, one of the purposes of an operating system is to handle the details of the operation of the hardware. This relieves application programs from having to manage these details and makes it easier to write applications. Almost all computers (including handheld computers, desktop computers, supercomputers, video game consoles) as well as some robots, domestic appliances (dishwashers, washing machines), and portable media players use an operating system of some type. [1] Some of the oldest models may however use an embedded operating system, that may be contained on a compact disk or other data storage device.
Operating systems offer a number of services to application programs and users. Applications access these services through application programming interfaces (APIs) or system calls. By invoking these interfaces, the application can request a service from the operating system, pass parameters, and receive the results of the operation. Users may also interact with the operating system with some kind of software user interface (UI) like typing commands by using command line interface (CLI) or using a graphical user interface (GUI, commonly pronounced “gooey”). For hand-held and desktop computers, the user interface is generally considered part of the operating system. On large multi-user systems like Unix and Unix-like systems, the user interface is generally implemented as an application program that runs outside the operating system. (Whether the user interface should be included as part of the operating system is a point of contention.)
Operating systems offer a number of services to application programs and users. Applications access these services through application programming interfaces (APIs) or system calls. By invoking these interfaces, the application can request a service from the operating system, pass parameters, and receive the results of the operation. Users may also interact with the operating system with some kind of software user interface (UI) like typing commands by using command line interface (CLI) or using a graphical user interface (GUI, commonly pronounced “gooey”). For hand-held and desktop computers, the user interface is generally considered part of the operating system. On large multi-user systems like Unix and Unix-like systems, the user interface is generally implemented as an application program that runs outside the operating system. (Whether the user interface should be included as part of the operating system is a point of contention.)
Thursday, June 25, 2009
HARDWARE PROTECTION
• When executing in kernel mode, the operating system has unrestricted access to both kernel and user’s memory.
• The load instructions for the base and limit registers are privileged instructions.
DUAL OPERATION
• Mode bit added to computer hardware to indicate the current mode: kernel (0) or user (1).
• When an interrupt or fault occurs hardware switches to kernel mode.
I/O PROTECTION
• All I/O instructions are privileged instructions.
• Given the I/O instructions are privileged, how does the user program perform I/O?
• System call – the method used by a process to request action by the operating system.
– Usually takes the form of a trap to a specific location in the interrupt vector.
– Control passes through the interrupt vector to a service routine in the OS, and the mode bit is set to kernel mode.
– The kernel verifies that the parameters are correct and legal, executes the request, and returns control to the instruction following the system call.
MEMORY PROTECTION
• Must provide memory protection at least for the interrupt vectorand the interrupt service routines.
• In order to have memory protection, add two registers that determine the range of legal addresses a program may access:
– base register – holds the smallest legal physical memory address.
– Limit register – contains the size of the range
• Memory outside the defined range is protected.
CPU PROTECTION
• Timer – interrupts computer after specified period to ensure operating system maintains control.
– Timer is decremented every clock tick.
– When timer reaches the value 0, an interrupt occurs.
• Timer commonly used to implement time sharing.
• Time also used to compute the current time.
• Load-timer is a privileged instruction.
• The load instructions for the base and limit registers are privileged instructions.
DUAL OPERATION
• Mode bit added to computer hardware to indicate the current mode: kernel (0) or user (1).
• When an interrupt or fault occurs hardware switches to kernel mode.
I/O PROTECTION
• All I/O instructions are privileged instructions.
• Given the I/O instructions are privileged, how does the user program perform I/O?
• System call – the method used by a process to request action by the operating system.
– Usually takes the form of a trap to a specific location in the interrupt vector.
– Control passes through the interrupt vector to a service routine in the OS, and the mode bit is set to kernel mode.
– The kernel verifies that the parameters are correct and legal, executes the request, and returns control to the instruction following the system call.
MEMORY PROTECTION
• Must provide memory protection at least for the interrupt vectorand the interrupt service routines.
• In order to have memory protection, add two registers that determine the range of legal addresses a program may access:
– base register – holds the smallest legal physical memory address.
– Limit register – contains the size of the range
• Memory outside the defined range is protected.
CPU PROTECTION
• Timer – interrupts computer after specified period to ensure operating system maintains control.
– Timer is decremented every clock tick.
– When timer reaches the value 0, an interrupt occurs.
• Timer commonly used to implement time sharing.
• Time also used to compute the current time.
• Load-timer is a privileged instruction.
STORAGE HEIRARCHY
• Storage systems organized in hierarchy.
– Speed
–cost
– volatility
• Caching – copying information into faster storage system; main memory can be viewed as a cache for secondary storage.
– Speed
–cost
– volatility
• Caching – copying information into faster storage system; main memory can be viewed as a cache for secondary storage.
STORAGE STRUCTURE
• Main memory – only large storage media that the CPU can access directly.
• Secondary storage – extension of main memory that provides large nonvolatile storage capacity.
• Magnetic disks – rigid metal or glass platters covered with magnetic recording material
– Disk surface is logically divided into tracks, which are subdivided into sectors.
– The disk controller determines the logical interaction between the device and the computer.
• Secondary storage – extension of main memory that provides large nonvolatile storage capacity.
• Magnetic disks – rigid metal or glass platters covered with magnetic recording material
– Disk surface is logically divided into tracks, which are subdivided into sectors.
– The disk controller determines the logical interaction between the device and the computer.
Wednesday, June 24, 2009
8.) MAIN MEMORY
-Refers to physicalmemory that is internal to thecomputer. The word main is used to distinguish it from external mass storage devices such as disk drives. Another term for main memory isRAM.
7.) DIFFERENCE OF RAM AND DRAM
-These terms all refer to different types of computer memory, or RAM - Random Access Memory. The "random" part means that any area of the memory can be communicated with. When people talk about how much memory or RAM their computer has, they are usually referring to DRAM (or in newer systems, SDRAM). (S)DRAM is a computer's main memory that holds onto information for the mictorprocessor. The "D" stands for dynamic, meaning the RAM needs to have the information it's holding continuously renewed or "refreshed". SDRAM (Synchronous DRAM) is a newer faster type of DRAM. Designed to keep up with today's high-speed microprocessors, SDRAM can typically run at the same speed as the overall system.
6.) DIRECT MEMORY ACCESS
-Direct memory access (DMA) is a feature of moder computers and microprocessors that allows certain hardware subsystems within the computer to access system memory for reading and/or writing independently of the central processing unit. Many hardware systems use DMA including disk drivecontrollers, graphics cards, network cards andsound cards. DMA is also used for intra-chip data transfer in multi-core processors, especially inmultiprocessor system-on-chips, where its processing element is equipped with a local memory (often called scratchpad memory) and DMA is used for transferring data between the local memory and the main memory. Computers that have DMA channels can transfer data to and from devices with much less CPU overhead than computers without a DMA channel. Similarly a processing element inside a multi-core processor can transfer data to and from its local memory without occupying its processor time and allowing computation and data transfer concurrency. Without DMA, using programmed input/output (PIO) mode for communication with peripheral devices, or load/store instructions in the case of multicore chips, the CPU is typically fully occupied for the entire duration of the read or write operation, and is thus unavailable to perform other work. With DMA, the CPU would initiate the transfer, do other operations while the transfer is in progress, and receive an interrupt from the DMA controller once the operation has been done. This is especially useful in real-time computingapplications where not stalling behind concurrent operations is critical. Another and related application area is various forms of stream processing where it is essential to have data processing and transfer in parallel, in order to achieve sufficient throughput.
4.) USER MODE
-In User mode, the executing code has no ability to directly access hardware or reference memory. Code running in user mode must delegate to system APIs to access hardware or memory. Due to the protection afforded by this sort of isolation, crashes in user mode are always recoverable. Most of the code running on your computer will execute in user mode.
Tuesday, June 23, 2009
2.) DIFFERENCE OF INTERRUPT AND TRAP AND THIER USE.
-An interrupt is generally initiated by an I/O device, and causes the CPU to stop what it's doing, save its context, jump to the appropriate interrupt service routine, complete it, restore the context, and continue execution. For example, a serial device may assert the interrupt line and then place an interrupt vector number on the data bus. The CPU uses this to get the serial device interrupt service routine, which it then executes as above.
-A trap is usually initiated by the CPU hardware. When ever the trap condition occurs (on arithmetic overflow, for example), the CPU stops what it's doing, saves the context, jumps to the appropriate trap routine, completes it, restores the context, and continues execution. For example, if overflow traps are enabled, adding two very large integers would cause the overflow bit to be set AND the overflow trap service routine to be initiated.
-A trap is usually initiated by the CPU hardware. When ever the trap condition occurs (on arithmetic overflow, for example), the CPU stops what it's doing, saves the context, jumps to the appropriate trap routine, completes it, restores the context, and continues execution. For example, if overflow traps are enabled, adding two very large integers would cause the overflow bit to be set AND the overflow trap service routine to be initiated.
3.) MONITOR MODE
-Monitor mode, or RFMON (Radio Frequency Monitor) mode, allows a computer with a wireless network interface card (NIC) to monitor all traffic received from the wireless network. Unlike promiscuous mode, which is also used for packet sniffing, monitor mode allows packets to be captured without having to associate with an access point or ad-hoc network first. Monitor mode only applies to wireless networks, while promiscuous mode can be used on both wired and wireless networks. Monitor mode is one of the six modes that 802.11 wireless cards can operate in: Master (acting as an access point), Managed (client, also known as station), Ad-hoc, Mesh, Repeater, and Monitor mode.
1.) BOOTSTRAP PROGRAM
-In computing, booting is a bootstrapping process that starts operating systems when the user turns on a computer system.
Most computer systems can only execute code found in the memory (ROM or RAM); modern operating systems are mostly stored on hard disk drives, LiveCDs and USB flash drive. Just after a computer has been turned on, it doesn't have an operating system in memory. The computer's hardware alone cannot perform complicated actions of the operating system, such as loading a program from disk on its own; so a seemingly irresolvable paradox is created: to load the operating system into memory, one appears to need to have an operating system already installed.
Most computer systems can only execute code found in the memory (ROM or RAM); modern operating systems are mostly stored on hard disk drives, LiveCDs and USB flash drive. Just after a computer has been turned on, it doesn't have an operating system in memory. The computer's hardware alone cannot perform complicated actions of the operating system, such as loading a program from disk on its own; so a seemingly irresolvable paradox is created: to load the operating system into memory, one appears to need to have an operating system already installed.
Saturday, June 20, 2009
5. Differentiate symmetric multi processing and asymmetric multiprocessing.
Symmetric multiprocessing - in computing, symmetric multiprocessing or SMP involves a multiprocessor computer-architecture where two or more identical processors can connect to a single shared main memory. Most common multiprocessor systems today use an SMP architecture. In the case of multi-core processors, the SMP architecture applies to the cores, treating them as separate processors.
SMP systems allow any processor to work on any task no matter where the data for that task are located in memory; with proper operating system support, SMP systems can easily move tasks between processors to balance the workload efficiently.
Asymmetric multiprocessing - Asymmetric multiprocessing or ASMP is a type of multiprocessing supported in DEC's VMS V.3 as well as a number of older systems including TOPS-10 and OS-360. It varies greatly from the standard processing model that we see in personal computers today. Due to the complexity and unique nature of this architecture, it was not adopted by many vendors or programmers during its brief stint between 1970 - 1980.
SMP systems allow any processor to work on any task no matter where the data for that task are located in memory; with proper operating system support, SMP systems can easily move tasks between processors to balance the workload efficiently.
Asymmetric multiprocessing - Asymmetric multiprocessing or ASMP is a type of multiprocessing supported in DEC's VMS V.3 as well as a number of older systems including TOPS-10 and OS-360. It varies greatly from the standard processing model that we see in personal computers today. Due to the complexity and unique nature of this architecture, it was not adopted by many vendors or programmers during its brief stint between 1970 - 1980.
3. What’s difference between batch systems, multi-programmed systems and time sharing systems?
batch system- is one in which jobs are bundled together with the instructions necessary to allow them to be processed without intervention.
multitasking- is a method by which multiple tasks, also known as processes, share common processing resources such as a CPU. In the case of a computer with a single CPU, only one task is said to be running at any point in time, meaning that the CPU is actively executing instructions for that task.
Time-sharing- is sharing a computing resource among many users by multitasking.
multitasking- is a method by which multiple tasks, also known as processes, share common processing resources such as a CPU. In the case of a computer with a single CPU, only one task is said to be running at any point in time, meaning that the CPU is actively executing instructions for that task.
Time-sharing- is sharing a computing resource among many users by multitasking.
2. Explain the goals of OS
-It is easier to define an operating system by what it does than what it is, but even this can be tricky. The primary goal of some operating system is convenience for the user. The primary goal of other operating system is efficient operation of the computer system. Operating systems and computer architecture have influenced each other a great deal. To facilitate the use of the hardware, researchers developed operating systems. Users of the operating systems then proposed changes in hardware design to simplify them. In this short historical review, notice how identification of operating-system problems led to the introduction of new hardware features.
Thursday, June 18, 2009
8.) Define the essential properties of the following types of OS.
A. batch
-Jobs with similar needs are batched together and run through the computer as a group, by an operator or automatic job sequencer. Performance is increased by attempting to keep CPU and I/O devices busy at all times through buffering, off-line operation, spooling, and multiprogramming.
B. time sharing
-sharing a computing resource among many users by multitasking Its introduction in the 1960s, and emergence as the prominent model of computing in the 1970s, represents a major historical shift in the history of computing. By allowing a large number of users to interact simultaneously on a single computer, time-sharing dramatically lowered the cost of providing computing, while at the same time making the computing experience much more interactive.
C. real timeReal
-Time Operating System (RTOS) is a multitasking operating system intended for real-time applications. Such applications include embedded systems (programmable thermostats, household appliance controllers), industrial robots, spacecraft, industrial control (see SCADA), and scientific research equipment.
D. network
-Network operating systems typically are used to run computers that act as servers. They provide the capabilities required for network operation. Network operating systems are also designed for client computers and provide functions so the distinction between network operating systems and stand alone operating systems is not always obvious.
E. distributed
-with the advent of computer networks, in which many computers are linked together and are able to communicate with one another, distributed computing became feasible. A distributed computation is one that is carried out on more than one machine in a cooperative manner. A group of linked computers working cooperatively on tasks.
F. handheld
-A handheld PC's operating system determines not only what you see onscreen, but also how you interact with the device and what kind of services you can get from it. The two dominant handheld OSes are Palm and Pocket PC but Symbian and Linux are both up and coming. To help you decide which OS you want on your next handheld, here's a breakdown of these four operating systems plus a few of our hardware picks to get you started.
-Jobs with similar needs are batched together and run through the computer as a group, by an operator or automatic job sequencer. Performance is increased by attempting to keep CPU and I/O devices busy at all times through buffering, off-line operation, spooling, and multiprogramming.
B. time sharing
-sharing a computing resource among many users by multitasking Its introduction in the 1960s, and emergence as the prominent model of computing in the 1970s, represents a major historical shift in the history of computing. By allowing a large number of users to interact simultaneously on a single computer, time-sharing dramatically lowered the cost of providing computing, while at the same time making the computing experience much more interactive.
C. real timeReal
-Time Operating System (RTOS) is a multitasking operating system intended for real-time applications. Such applications include embedded systems (programmable thermostats, household appliance controllers), industrial robots, spacecraft, industrial control (see SCADA), and scientific research equipment.
D. network
-Network operating systems typically are used to run computers that act as servers. They provide the capabilities required for network operation. Network operating systems are also designed for client computers and provide functions so the distinction between network operating systems and stand alone operating systems is not always obvious.
E. distributed
-with the advent of computer networks, in which many computers are linked together and are able to communicate with one another, distributed computing became feasible. A distributed computation is one that is carried out on more than one machine in a cooperative manner. A group of linked computers working cooperatively on tasks.
F. handheld
-A handheld PC's operating system determines not only what you see onscreen, but also how you interact with the device and what kind of services you can get from it. The two dominant handheld OSes are Palm and Pocket PC but Symbian and Linux are both up and coming. To help you decide which OS you want on your next handheld, here's a breakdown of these four operating systems plus a few of our hardware picks to get you started.
7.) Differentiate the design issues of OS between a stand alone PC’s and a workstation connected to a network.
-Stand-alone PC - a desktop or laptop computer that is used on its own without requiring a connection to a local area network (LAN) or wide area network (WAN). Although it may be connected to a network, it is still a stand-alone PC as long as the network connection is not mandatory for its general use.Workstation - is a high-end microcomputer designed for technical or scientific applications. Intended primarily to be used by one person at a time, they are commonly connected to a local area network and run multi-user operating systems.
6.) Differentiate client-server system and peer to peer system?
-Client/server describes the relationship between two computer programs in which one program, the client, makes a service request from another system, the server, which fulfils the request. In a network, the client/server model provides a convenient way to efficiently interconnect programs that are distributed across different locations
Another structure for distributes system is the peer - to peer (P2P) system model. In this model, clients and servers are not distinguished from one another; instead, all nodes within the system may act as either client or a server, depending on whether it is requesting or providing a service.
In client server system, the server is a bottle neck; but in a peer-to peer system, services can be provided by several nodes throughout the network.
Another structure for distributes system is the peer - to peer (P2P) system model. In this model, clients and servers are not distinguished from one another; instead, all nodes within the system may act as either client or a server, depending on whether it is requesting or providing a service.
In client server system, the server is a bottle neck; but in a peer-to peer system, services can be provided by several nodes throughout the network.
4.) Advantage of parallel system?
-In terms of disproportional, Parallel systems usually give results which fall somewhere between pure plurality/majority and pure PR systems. One advantage is that, when there are enough PR seats, small minority parties which have been unsuccessful in the plurality/majority elections can still be rewarded for their votes by winning seats in the proportional allocation. In addition, a Parallel system should, in theory, fragment the party system less than a pure PR electoral system.
Wednesday, February 25, 2009
zQuestions to be answered:
1.) What is the reason for technicians to wear special wrist grounding straps?
=A wrist grounding strap is used to prevent electrostatic discharge when handling computer components. Just like a shock when walking on carpet can carry several thousand volts, it destroys computer components.
WWW.WikiAnswer.com
2.)After installing a new computer component why is it important to obtain the most current driver for it?
=
3.) What are the steps required to install a peripheral device?
=It doesn't work for all device, only for standard ones. If you have a standard type device then just follow instractions, choose automatic and OS will fine it. If it didn't work you will need a driver. Which you can find on manufacture website. Usually it has instructions.
http://www.wikianswer.com/
4.)If a newly installed peripheral device does not function properly what steps can be taken to correct the problem?
=But it can be because of many different reasons. First, the device doesn't work properly; second, the user remove drivers; third, bug in the software and so on. If device is working properly, what you can do is turn everything off. Then start the pc, wait while it's booting up. After you logged on and windows started turn your device. If nothing was broken it will work again.
http://www.wikianswer.com/
5.) Explain the technique used to help protect data on a hard drive when doing a clean install?
=One of the techniques available to help protect data is to divide the hard drive intomultiple partitions. With a clean install, many technicians prefer to create one.
http://eskilstuna.se/upload/85680/Svar%20kapitel%202.pdf
6.) Explain what a software patch is.
=A patch is a small piece of software designed to fix problems with or update a compyter program or its supporting data. This includes fixing bugs, replacing graphics and improving the usability or performance. Though meant to fix problems, poorly designed patches can sometimes introduce new problems (see software regressions).
http://en.wikipedia.org/wiki/Patch_(computing)
1.) What is the reason for technicians to wear special wrist grounding straps?
=A wrist grounding strap is used to prevent electrostatic discharge when handling computer components. Just like a shock when walking on carpet can carry several thousand volts, it destroys computer components.
WWW.WikiAnswer.com
2.)After installing a new computer component why is it important to obtain the most current driver for it?
=
3.) What are the steps required to install a peripheral device?
=It doesn't work for all device, only for standard ones. If you have a standard type device then just follow instractions, choose automatic and OS will fine it. If it didn't work you will need a driver. Which you can find on manufacture website. Usually it has instructions.
http://www.wikianswer.com/
4.)If a newly installed peripheral device does not function properly what steps can be taken to correct the problem?
=But it can be because of many different reasons. First, the device doesn't work properly; second, the user remove drivers; third, bug in the software and so on. If device is working properly, what you can do is turn everything off. Then start the pc, wait while it's booting up. After you logged on and windows started turn your device. If nothing was broken it will work again.
http://www.wikianswer.com/
5.) Explain the technique used to help protect data on a hard drive when doing a clean install?
=One of the techniques available to help protect data is to divide the hard drive intomultiple partitions. With a clean install, many technicians prefer to create one.
http://eskilstuna.se/upload/85680/Svar%20kapitel%202.pdf
6.) Explain what a software patch is.
=A patch is a small piece of software designed to fix problems with or update a compyter program or its supporting data. This includes fixing bugs, replacing graphics and improving the usability or performance. Though meant to fix problems, poorly designed patches can sometimes introduce new problems (see software regressions).
http://en.wikipedia.org/wiki/Patch_(computing)
Friday, January 30, 2009
Windows 2000 Professional Microsoft released this new Windows version 5.0, Build 2195 in February 2000. It is the desktop operating system of the new Windows 2000 platform for x86 architecture and be completed by the versions Windows 2000 Server, Windows 2000 Advanced Server and Windows 2000 Datacenter Server. As a minimum requierement for the installation a Pentium processor, 32 mbyte main memory and 650 mbyte of free hard disk storage are needed. Microsoft had planned to develop also a operating system version for the Alpha architecture, the plans were stopped after an announcement of Compaq. Compaq restricted the support to Windows NT 4.0 with service pack 6 and not higher at 1999-08-25. Microsoft stopped the development plans for the Windows 2000 32- bit of Alpha version after that. Windows 2000 unites defined roughly the user-friendliness, pug & play and USB device support of Windows 98 and the safety and stability of the Windows NT family. The update to this new operating system is possible from Windows 95, 98 and Windows NT 3.51, 4.0. It is a multitasking, multiprocessing operating system and supports up to 2 processors of the x86 32- bit and 64 bit architecture with SMP. Threads or processes can choose between the available processors. Beside the complete revision new features and many improvements are integrated. The result is high compatibility, simplified administration, increased hardware support with over 7,000 devices, file administration and extended security functions. Applications for Windows 9x are only supported restrictedly. The installation is possible from CD-ROM or over the network from a file server. The virtual addressable storage is 4 gbyte and is managed by the Virtual Memory manager (VMM). VMM assigns the addressable storage on the actually available physical memory and the memory page file (pagefile.sys) on hard disk. The field of application of this operating system is suitable as a single user computer or as a client in company networks. The operating system is enhanced with the game interface DirectX 7.0, the Internet Explorer 5.0 made access to the Internet possible. Windows 2000 authenticates the user first at the access to files, printers or other computers. Networks are supported with the protocols TCP/IP, NWLink and AppleTalk. Windows 2000 supports the data interchange in decentralised working groups and central domains. Furthermore the Registry consists as in Windows NT 4.0 before of the system files SAM, SECURITY, SOFTWARE and SYSTEM. The hierarchical database saves information of the hardware and applications as well as configuration settings. The following basic services are in Windows 2000 Prof. installed. The SFC (System File Protection) offers protection from overwrite of Windows system files. It is possible to create hardware profiles for different hardware configurations with the settings of all devices and services. NTFS is used as file system in the new version 5. The specification of user rights is possible for files and directories on file system level, file compression in real time, disk storage quotas (Quotas) and encrypting with EFS (Encrypting File System) can also be used. At the specification of rights the Access Control List (ACL) is stored with every file and every directory. The compression and encoding exclude each other, only one of the options on the same object can be used. Furthermore the FAT/FAT32 file system is supported. Windows 2000 Prof. is also suitable for mobile use on notebook computers. With the complete support of the technologies APM and ACPI an effective energy management and thus lower electricity consumption is possible. With the Suspend to Disk function the computer can be put into a power saving mode and is in the same condition as before after short reactivation time. An assistant supports the user at the administration of the network connections, with use of VPN (Virtual Private Network) and IPSec (Internet Protocol Security) secure mobile access to company networks is possible. The printer administration was simplified with an assistant. 2004-02-13 announced Microsoft that parts of the source code of Windows 2000 has leaked on the Internet. The source code appeared illegally in peer-to-peer file sharing networks, Microsoft said to use the full law to protect the stolen property. 2003-06-25 the Service Pack 4 eliminates 675 bugs appeared since the last service pack. New is the support for USB 2.0 device connections. - unattended installation of the operating system via script possible - different options for Windows start like "safe mode" and "last as good known configuration" - booting from the Windows 2000 CD-ROM offers repair of the operating system or recovery console - supports the display of the desktop on up to 10 monitors - task planner for time controlled executing of programmes - utilities for hard disk like defragmentation and check on disk errors - event viewer for protocolling of application, security and system events - backup tool for data safety and recovery - Microsoft Management Console (MMC), administration of the local or remote computer, expandable by SnapIns - support for local and predefined user accounts, domain user accounts - ActiveDirectory directory service available if client is member in Windows 2000 domain - New protocols for a secure authentication in the network are EAP, RADIUS, IPSec, L2TP and BAP 

Thursday, January 29, 2009
Step 17 - Finally you need to check if all your hardware has been detected correctly. You can do so by checking your device manager. To access device manager click Start menu -> Control panel -> System -> Device manager. You will see all your hardware listed as shown below. You need to check if you have any yellow exclamtion marks next to the name of the device similar to "USB 10/100 LAN" on image below. This indicates the driver has not been installed for this device.
At this stage you need to install Windows Vista drivers by double clicking on "USB 10/100 LAN" or your device. The properties dialog box will appear. Click on Reinstall Driver. Then you can choose wether you want to install the driver from the internet (if available) or install manually from a CD or other media
Once you have removed all the yellow exclamtion marks from the device manager your Windows Vista configuration would be fully complete. 
At this stage you need to install Windows Vista drivers by double clicking on "USB 10/100 LAN" or your device. The properties dialog box will appear. Click on Reinstall Driver. Then you can choose wether you want to install the driver from the internet (if available) or install manually from a CD or other media
Once you have removed all the yellow exclamtion marks from the device manager your Windows Vista configuration would be fully complete.

Next - How to install Windows Vista Page 3

Step 14 - Windows now runs a benchmark type of application which checks the performance of your system. You will see a status bar at bottom which shows the progress. Once the process is complete you will be presented with the logon screen.

Next screen presents you to select your computers current location. You can choose between home, work, public location. Choose home to continue. You will finally get a "Thank you" screen which confirms the end of the interactive installation process. This is not the end of the setup process. There are still many after installation configuration to be done. Click next to continue.
Step 10 - After installation copy process is complete you are presented with the Setup Windows dialogue box as show below. At this stage you need to choose a user name, password and a picture for your user account. The account you create here is the Administrator account which is the main account for your Windows Vista that has all the privilages. Click next continue. 

Step 9 - Windows starts the installation process and starts copying all the necessary files to your hard drive as shown on the image below. It will go through various stages of the setup and will reboot your system few times. When your PC reboots it attempts to boot from CD as its the first boot device. Do not press any key during the boot prompt so Windows Vista will continue with the installation by booting from your hard drive. 

Step 8 - Choose where you would like to install Windows Vista. If you have a new upartitioned hard drive you would get your hard drive listed as shown on the image below. If have have an old hard drive with data or other partitions it will show up as logical drives. You can select the drive options (advaced) to format, delete, or create new partions. Because I am using a single new hard drive i will select next to continue. Windows will create a partition and format it using NTFS files system. 

Step 6 - Tick "I accept the licence terms" and press next. 
Next - How to install Windows Vista Page 2

Next - How to install Windows Vista Page 2
Step 5 - If you do not enter the product key you can still proceed with the installation in which case Windows will ask you which version of Vista you have purchased. Windows Vista Home Basic, Home Premium, Ultimate, Business etc. Select the version you have purchased and click next.
Please note, although you can select any version of Windows and proceed to next stage. It is not good idea to select a different version to the one you have purchased becuase you will not be able to activate Windows at a later stage. Windows Vista can detect which version you have purchased once you enter your product key. 
Please note, although you can select any version of Windows and proceed to next stage. It is not good idea to select a different version to the one you have purchased becuase you will not be able to activate Windows at a later stage. Windows Vista can detect which version you have purchased once you enter your product key.

1.2 Screenshots on Windows Vista Installation

This step-by-step guide demonstrates how to install Windows Vista.
The best way to install Windows Vista is to do a clean install. It is not difficult to perform a clean installation. Before you perform the installation I recommend that you check Windows Vista System Requirments list to ensure that your hardware is supported by Vista. If you dont have Windows Vista drivers for all your hardware, it is a good idea to download all the drivers from the hardware manufacturers website and save all the necessary drivers on a CD-R before you start the installation.
Windows Vista DVD is bootable. In order to boot from the DVD you need to set the boot sequence. Look for the boot sequence under your BIOS setup and make sure that the first boot device is set to CD-ROM/DVD-ROM.
The best way to install Windows Vista is to do a clean install. It is not difficult to perform a clean installation. Before you perform the installation I recommend that you check Windows Vista System Requirments list to ensure that your hardware is supported by Vista. If you dont have Windows Vista drivers for all your hardware, it is a good idea to download all the drivers from the hardware manufacturers website and save all the necessary drivers on a CD-R before you start the installation.
Windows Vista DVD is bootable. In order to boot from the DVD you need to set the boot sequence. Look for the boot sequence under your BIOS setup and make sure that the first boot device is set to CD-ROM/DVD-ROM.
Step 1 - Place Windows Vista DVD in your dvd-rom drive and start your PC. Windows Vista will start to boot up and you will get the following progress bar.

Wednesday, January 28, 2009

Step 9 - Now you will see both partition listed. Partition 1 (C: Drive) 6000MB and Partition 2 (E: Drive) 2180MB. You will also have 8MB of unpartitioned space. Don't worry about that. Just leave it how its is. Windows normally has some unpartitioned space. You might wonder what happened to D: drive. Windows has automatically allocated D: drive to CD/DVD-ROM.Select Partition 1 (C: Drive) and press Enter.

Windows will show the total size of the hard drive and ask you how much you want to allocate for the partition you are about to create. I will choose 6000MB. You will then get the screen below. Notice it shows C: Partition 1 followed by the size 6000 MB. This indicates the partition has been created. We still have an unpartitioned space of 2189MB. Next heighlight the unpartitioned space by pressing down the arrow key. Then press C to create another partition. You will see the total space available for the new partition. Just choose all the space left over, in our case 2180MB.

Step 8 - This step is very important. Here we will create the partition where Windows will be installed. If you have a brand new unformatted drive you will get a screen similar to below. In our case the drive size is 8190MB. We can choose to install Windows in this drive without creating a partition, hence use the entire size of the drive. If you wish to do this you can just press enter and Windows will automatically partition and format the drive as one large drive.However for this demonstration I will create two partition. The first partition will be 6000MB (C: drive) and second partition would be 2180MB (E: drive). By creating two partition we can have one which stores Windows and Applications and the other which stores our data. So in the future if anything goes wrong with our Windows install such as virus or spyware we can re-install Windows on C: drive and our data on E: drive will not be touched. Please note you can choose whatever size partition your like. For example if you have 500GB hard drive you can have two partition of 250GB each.Press C to create a partition.

Step 2 - At this stage it will ask you to press F6 if you want to install a third party Raid or SCSI driver. If you are using a an IDE Hard Drive then you do not need to press F6. If you are using a SCSI or SATA Hard drive then you must press F6 otherwise Windows will not detect your Hard Drive during the installation. Please make sure you have the Raid drivers on a floppy disk. Normally the drivers are supplied on a CD which you can copy to a floppy disk ready to be installed. If you are not sure how to do this then please read your motherboard manuals for more information.
1.1 Screenshots of Windows XP
Thursday, January 15, 2009
1.4 Latest Expansion Slots
 BLADECENTER HS20 FC EXPANSION CARD
BLADECENTER HS20 FC EXPANSION CARD
Manufacturer: IBM
Part Number: 48P7061
Specifications: Data transfer rate: 2.12 Gbps ; Connectivity technology: Wired See full specs
 BLADECENTER HS20 FC EXPANSION CARD
BLADECENTER HS20 FC EXPANSION CARDManufacturer: IBM
Part Number: 48P7061
Specifications: Data transfer rate: 2.12 Gbps ; Connectivity technology: Wired See full specs
1.3 Notebooks/Laptops
Intel® Centrino® 2 Processor Technology for Laptop ComputersThe best notebooks have Intel® Centrino® 2 processor technology insideΔ1Intel’s NEWEST and BEST performing notebook technology includes: • Up to 50% faster performance when multitasking‡1 • Optimized for wireless - up to 2X greater range and up to 5X better Wi-Fi performance, with optional built-in WiMAX to equip your notebook for the future of metro-wide broadband wirelessΔ2 Δ3 • Designed for the longest possible battery life • Up to 90% faster performance on intensive multimedia applications like HD video encodingΔ

Intel® Centrino® 2 Processor Technology for Laptop ComputersThe best notebooks have Intel® Centrino® 2 processor technology insideΔ1Intel’s NEWEST and BEST performing notebook technology includes: • Up to 50% faster performance when multitasking‡1 • Optimized for wireless - up to 2X greater range and up to 5X better Wi-Fi performance, with optional built-in WiMAX to equip your notebook for the future of metro-wide broadband wirelessΔ2 Δ3 • Designed for the longest possible battery life • Up to 90% faster performance on intensive multimedia applications like HD video encodingΔ
1.2 Servers

Intel® Xeon® processor 7400 series
Extending today's lead in virtualization performance with built-in hardware assisted features and breakthrough gains in performance and energy efficiency.
Built for data-demanding enterprise applications with up to 6 cores and a large shared 16MB L3 cache per processor, enabling more transactions per server
More headroom, improved reliability, and the highest scalability available for large scale server consolidation and business-critical virtualization.

Intel® Xeon® processor 7400 series
Extending today's lead in virtualization performance with built-in hardware assisted features and breakthrough gains in performance and energy efficiency.
Built for data-demanding enterprise applications with up to 6 cores and a large shared 16MB L3 cache per processor, enabling more transactions per server
More headroom, improved reliability, and the highest scalability available for large scale server consolidation and business-critical virtualization.
Wednesday, January 14, 2009
Latest Server:

Hawking Technologies 1-Port USB 2.0 Print Server for ...The HMPS1U connects your USB 1.1 multifunction printer to your existing home or office network,

Hawking Technologies 1-Port USB 2.0 Print Server for ...The HMPS1U connects your USB 1.1 multifunction printer to your existing home or office network,
Latest Processor
Latest Processor:
 There are two main competitors in the processor market. AMD and Intel. AMD makes the Athlon and Duron processors, while Intel makes the Celeron and Pentium series of processors. Both these chips can run the same operating systems same software, same peripherals although they will require different motherboards and possibly different memory. It is not very easy to compare the performance of the two either. A 2 GHz Athlon processor from AMD will not run at the same speed as a 2 GHz processor from Intel. In fact the latest AMD models run at 2.2GHz and the latest Intel P4s run at 3.2GHz and give a similar performance. One thing that may help guide you though is AMDs model naming convention. For example the Athlon XP 2000+ will be roughly equivalent to the 2000MHz (2 GHz) Pentium 4. The AMD Athlon XP 1700+ is roughly equivalent to the 1.7Ghz Pentium 4. In both these cases the AMD is we believe slightly faster. It also tends to be slightly cheaper.
There are two main competitors in the processor market. AMD and Intel. AMD makes the Athlon and Duron processors, while Intel makes the Celeron and Pentium series of processors. Both these chips can run the same operating systems same software, same peripherals although they will require different motherboards and possibly different memory. It is not very easy to compare the performance of the two either. A 2 GHz Athlon processor from AMD will not run at the same speed as a 2 GHz processor from Intel. In fact the latest AMD models run at 2.2GHz and the latest Intel P4s run at 3.2GHz and give a similar performance. One thing that may help guide you though is AMDs model naming convention. For example the Athlon XP 2000+ will be roughly equivalent to the 2000MHz (2 GHz) Pentium 4. The AMD Athlon XP 1700+ is roughly equivalent to the 1.7Ghz Pentium 4. In both these cases the AMD is we believe slightly faster. It also tends to be slightly cheaper.
 There are two main competitors in the processor market. AMD and Intel. AMD makes the Athlon and Duron processors, while Intel makes the Celeron and Pentium series of processors. Both these chips can run the same operating systems same software, same peripherals although they will require different motherboards and possibly different memory. It is not very easy to compare the performance of the two either. A 2 GHz Athlon processor from AMD will not run at the same speed as a 2 GHz processor from Intel. In fact the latest AMD models run at 2.2GHz and the latest Intel P4s run at 3.2GHz and give a similar performance. One thing that may help guide you though is AMDs model naming convention. For example the Athlon XP 2000+ will be roughly equivalent to the 2000MHz (2 GHz) Pentium 4. The AMD Athlon XP 1700+ is roughly equivalent to the 1.7Ghz Pentium 4. In both these cases the AMD is we believe slightly faster. It also tends to be slightly cheaper.
There are two main competitors in the processor market. AMD and Intel. AMD makes the Athlon and Duron processors, while Intel makes the Celeron and Pentium series of processors. Both these chips can run the same operating systems same software, same peripherals although they will require different motherboards and possibly different memory. It is not very easy to compare the performance of the two either. A 2 GHz Athlon processor from AMD will not run at the same speed as a 2 GHz processor from Intel. In fact the latest AMD models run at 2.2GHz and the latest Intel P4s run at 3.2GHz and give a similar performance. One thing that may help guide you though is AMDs model naming convention. For example the Athlon XP 2000+ will be roughly equivalent to the 2000MHz (2 GHz) Pentium 4. The AMD Athlon XP 1700+ is roughly equivalent to the 1.7Ghz Pentium 4. In both these cases the AMD is we believe slightly faster. It also tends to be slightly cheaper. Latest Processor
1.1 Desktop Computers

Extreme Gaming with the Intel® Core™ i7 Processor Extreme EditionFor DesktopsThe ultimate immersive gaming experience Conquer the world of extreme gaming with the highest performing desktop processor on the planet: the Intel® Core™ i7 processor Extreme Edition.‡1 With intelligent multi-core technology that kicks into overdrive as your activity becomes more intense, it delivers breakthrough performance in gaming. Plus, multitask demanding applications up to 25% faster‡2 and unleash amazing power for digital media creation.

Extreme Gaming with the Intel® Core™ i7 Processor Extreme EditionFor DesktopsThe ultimate immersive gaming experience Conquer the world of extreme gaming with the highest performing desktop processor on the planet: the Intel® Core™ i7 processor Extreme Edition.‡1 With intelligent multi-core technology that kicks into overdrive as your activity becomes more intense, it delivers breakthrough performance in gaming. Plus, multitask demanding applications up to 25% faster‡2 and unleash amazing power for digital media creation.
Subscribe to:
Posts (Atom)


















