>For communication and synchronization
–Shared memory
–OS provided IPC
>Message system
–no need for shared variable
– two operations
•send(message) – message size fixed or variable
•receive(message)
>If P and Q wish to communicate, they need to
–establish a communication link between them
–exchange messages via send/receive
>Implementation of communication link
–physical (e.g., shared memory, hardware bus)
–logical (e.g., logical properties)
.....MAHAL KITA PERO MAS MAHAL KO ANG SARILI KO!!!
Thursday, July 16, 2009
4.) COOPERATING PROCESSES
>Advantages of process cooperation
–Information sharing
–Computation speed-up
–Modularity
–Convenience
>Independent process cannot affect/be affected by the execution of another process, cooperating ones can
>Issues
–Communication
–Avoid processes getting into each other’s way
–Ensure proper sequencing when there are dependencies
>Common paradigm: producer-consumer
–unbounded-buffer - no practical limit on the size of the buffer
–bounded-buffer - assumes fixed buffer size
–Information sharing
–Computation speed-up
–Modularity
–Convenience
>Independent process cannot affect/be affected by the execution of another process, cooperating ones can
>Issues
–Communication
–Avoid processes getting into each other’s way
–Ensure proper sequencing when there are dependencies
>Common paradigm: producer-consumer
–unbounded-buffer - no practical limit on the size of the buffer
–bounded-buffer - assumes fixed buffer size
3.) OPERATION PROCESS
A.) PROCESS ON CREATION
Parent process creates children processes, which, in turn create other processes, forming a tree of processes.
Resource sharing:
>Parent and children share all resources.
>Children share subset of parent’s resources.
>Parent and child share no resources.
Execution:
>Parent and children execute concurrently.
>Parent waits until children terminate.
B.) PROCESS TERMINATION
>Process executes last statement and asks the operating system to delete it (exit).
>Output data from child to parent (via wait).
>Process’ resources are deallocated by operating system.
>Parent may terminate execution of children processes (abort).
>Child has exceeded allocated resources.
>Task assigned to child is no longer required.
>Parent is exiting.
>Operating system does not allow child to continue if its parent terminates.
>Cascading termination.
>In Unix, if parent exits children are assigned init as parent
Parent process creates children processes, which, in turn create other processes, forming a tree of processes.
Resource sharing:
>Parent and children share all resources.
>Children share subset of parent’s resources.
>Parent and child share no resources.
Execution:
>Parent and children execute concurrently.
>Parent waits until children terminate.
B.) PROCESS TERMINATION
>Process executes last statement and asks the operating system to delete it (exit).
>Output data from child to parent (via wait).
>Process’ resources are deallocated by operating system.
>Parent may terminate execution of children processes (abort).
>Child has exceeded allocated resources.
>Task assigned to child is no longer required.
>Parent is exiting.
>Operating system does not allow child to continue if its parent terminates.
>Cascading termination.
>In Unix, if parent exits children are assigned init as parent
2.) PROCESS SHEDULING
A.) SCHEDULING QUEUSE
>Job queue – set of all processes in the system.
>Ready queue – set of all processes residing in main memory, ready and waiting to >Execute.Device queues – set of processes waiting for an I/O device.
>Processes migrate between the various queues.
B.) SCHEDULERS
>Long-term scheduler (or job scheduler) – selects which processes should be brought into the ready queue.
>Short-term scheduler (or CPU scheduler) – selects which process should be executed next and allocates CPU.
>Short-term scheduler is invoked very frequently (milliseconds) fi (must be fast).
>Long-term scheduler is invoked very infrequently (seconds, minutes) fi (may be slow).
>The long-term scheduler controls the degree of multiprogramming.
>Processes can be described as either:
>I/O-bound process – spends more time doing I/O than computations, many short CPU bursts.
>CPU-bound process – spends more time doing computations; few very long CPU bursts.
C.) CONTEXT SWITCH
>When CPU switches to another process, the system must save the state of the old process and load the saved state for the new process.
>Context-switch time is overhead; the system does no useful work while switching.
>Time dependent on hardware support.
>Job queue – set of all processes in the system.
>Ready queue – set of all processes residing in main memory, ready and waiting to >Execute.Device queues – set of processes waiting for an I/O device.
>Processes migrate between the various queues.
B.) SCHEDULERS
>Long-term scheduler (or job scheduler) – selects which processes should be brought into the ready queue.
>Short-term scheduler (or CPU scheduler) – selects which process should be executed next and allocates CPU.
>Short-term scheduler is invoked very frequently (milliseconds) fi (must be fast).
>Long-term scheduler is invoked very infrequently (seconds, minutes) fi (may be slow).
>The long-term scheduler controls the degree of multiprogramming.
>Processes can be described as either:
>I/O-bound process – spends more time doing I/O than computations, many short CPU bursts.
>CPU-bound process – spends more time doing computations; few very long CPU bursts.
C.) CONTEXT SWITCH
>When CPU switches to another process, the system must save the state of the old process and load the saved state for the new process.
>Context-switch time is overhead; the system does no useful work while switching.
>Time dependent on hardware support.
1.) THE CONCEPTS OF PROCESS
A.) PROCESS STATE
-As a process executes, it changes state
new: The process is being created.F running: Instructions are being executed.
waiting: The process is waiting for some event to occur.
ready: The process is waiting to be assigned to a processor
terminated: The process has finished execution.
B.) PROCESS CONTROL BLACK
-Information associated with each process.
>Process ID
>Process state
>Program countern CPU registers
>CPU scheduling information
>Memory-management information
>Accounting information
>I/O status information
C.) THREADS
-Each process provides the resources needed to execute a program. A process has a virtual address space, executable code, open handles to system objects, a security context, a unique process identifier, environment variables, a priority class, minimum and maximum working set sizes, and at least one thread of execution. Each process is started with a single thread, often called the primary thread, but can create additional threads from any of its threads.
-As a process executes, it changes state
new: The process is being created.F running: Instructions are being executed.
waiting: The process is waiting for some event to occur.
ready: The process is waiting to be assigned to a processor
terminated: The process has finished execution.
B.) PROCESS CONTROL BLACK
-Information associated with each process.
>Process ID
>Process state
>Program countern CPU registers
>CPU scheduling information
>Memory-management information
>Accounting information
>I/O status information
C.) THREADS
-Each process provides the resources needed to execute a program. A process has a virtual address space, executable code, open handles to system objects, a security context, a unique process identifier, environment variables, a priority class, minimum and maximum working set sizes, and at least one thread of execution. Each process is started with a single thread, often called the primary thread, but can create additional threads from any of its threads.
Thursday, July 9, 2009
QUIZ NUMBER 3
1.) WHAT ARE THE MAJOR ACTIVITIES OF THE O.S WITH REGARDS TO PROCESS MANAGEMENT.
- Process creation and deletion
- Process suspension and resumption
- Provision of management for:
- Process synchornization
- Process communication
- Deadlack handling
2.) WHAT ARE THE MAJOR ACTIVITIES OF THE O.S WITH REGARDS TO MEMORY MANAGEMENT.
- Keep track of w/ parts of memory are curently being used and by whom.
- Decide w/c porcess to load when memory space becomes avalable.
- Allocate and dellocate memory space as needed.
3.) WHAT ARE THE MAJOR ACTIVITIES OF THE O.S WITH REGARDS TO SECONDARY-STORAGE MANAGEMENT.
- Free space management.
- Storage allocation.
- Disk scheduling.
4.) WHAT ARE THE MAJOR ACTIVITIES OF THE O.S WITH REGARDS TO FILE MANAGEMENT.
- File creation and deletion.
- Directory creation and deletion.
- Support of primitives for manipulating files and directories.
- Mapping files onto secondary storage.
- File backup on stable (volatile) storage media.
5.) WHAT IS THE PURPOSE OF THE COMMAND INTERPRETER
- Serves as the interface between the user and the operating system.
- User friendly, mouse based windows environment in the macintosh and in microsoft windows.
- Many command are given to the operating system by control statement with deals.
- Program that read and interpreters control statements is called variously.
Tuesday, July 7, 2009
SYSTEM BOOT
Operating system must be made available to hardware so hardware can start it
Small piece of code – bootstrap loader, locates the kernel, loads it into memory, and starts it
Sometimes two-step process where boot block at fixed location loads bootstrap loader
When power initialized on system, execution starts at a fixed memory location
Firmware used to hold initial boot code
Small piece of code – bootstrap loader, locates the kernel, loads it into memory, and starts it
Sometimes two-step process where boot block at fixed location loads bootstrap loader
When power initialized on system, execution starts at a fixed memory location
Firmware used to hold initial boot code
VIRTUAL MACHINE
• A virtual machine takes the layered approach to its logicalconclusion. It treats hardware and the operating system kerneas though they were all hardware.
• A virtual machine provides an interface identical to theunderlying bare hardware.
• The operating system creates the illusion of multipleprocesses, each executing on its own processor with its own(virtual) memory.
• The resources of the physical computer are shared to createthe virtual machines.
– CPU scheduling can create the appearance that usershave their own processor.
– Spooling and a file system can provide virtual card readeand virtual line printers.
– A normal user time-sharing terminal serves as the virtualmachine operator’s console.
IMPLEMENTATION OF VIRTUAL MACHINE
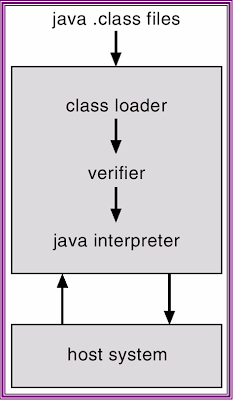
-Interpretation of Java bytecode results in slow execution of program.First version of Java Virtual Machine(JVM) implementation was relied on interpretation techniques. On the other hand performance can be improved by translating the Java bytecode into machine code by a Just-In-Time(JIT) compiler and this technique is being integrated into most JVM implementations. Java is an automatic garbage collected language, freeing the programmer from the explicit memory management. Garbage collection "pause" time can be reduced by using a generational garbage collection. This thesis describes an implementation of a JVM. The specific contributions made in this thesis include: development of a Just-In-Time(JIT) compiler using DAG construction technique, a bytecode interpreter, a generational garbage collector. Our implementation can execute Java bytecode either by an interpreter or the bytecode can be translated into machine code using the JIT compiler and the translated code is directly executed by the processor. We have implemented the Java Native Interface (JNI) to enable using C and assembly language programs with Java.
BENEFITS OF VIRTUAL MACHINE
-Virtual machines have been around for a long time but they really have not become common place in many development shops. It is unfortunate since virtual machines provide so many benefits to developers and testers alike. This article will discuss some of the benefits of virtual machines and review two of the most popular virtual machine software packages available for Windows.
EXAMPLE OF VIRTUAL MACHINE
-
• A virtual machine provides an interface identical to theunderlying bare hardware.
• The operating system creates the illusion of multipleprocesses, each executing on its own processor with its own(virtual) memory.
• The resources of the physical computer are shared to createthe virtual machines.
– CPU scheduling can create the appearance that usershave their own processor.
– Spooling and a file system can provide virtual card readeand virtual line printers.
– A normal user time-sharing terminal serves as the virtualmachine operator’s console.
IMPLEMENTATION OF VIRTUAL MACHINE
-Interpretation of Java bytecode results in slow execution of program.First version of Java Virtual Machine(JVM) implementation was relied on interpretation techniques. On the other hand performance can be improved by translating the Java bytecode into machine code by a Just-In-Time(JIT) compiler and this technique is being integrated into most JVM implementations. Java is an automatic garbage collected language, freeing the programmer from the explicit memory management. Garbage collection "pause" time can be reduced by using a generational garbage collection. This thesis describes an implementation of a JVM. The specific contributions made in this thesis include: development of a Just-In-Time(JIT) compiler using DAG construction technique, a bytecode interpreter, a generational garbage collector. Our implementation can execute Java bytecode either by an interpreter or the bytecode can be translated into machine code using the JIT compiler and the translated code is directly executed by the processor. We have implemented the Java Native Interface (JNI) to enable using C and assembly language programs with Java.
BENEFITS OF VIRTUAL MACHINE
-Virtual machines have been around for a long time but they really have not become common place in many development shops. It is unfortunate since virtual machines provide so many benefits to developers and testers alike. This article will discuss some of the benefits of virtual machines and review two of the most popular virtual machine software packages available for Windows.
EXAMPLE OF VIRTUAL MACHINE
-

SYSTEM GENARATION (SYSGEN)
> Operating systems are designed to run on any of a class of machines; the system must be configured for each specific computer siten SYSGEN program obtains information concerning the specific configuration of the hardware systemn Booting
– starting a computer by loading the kerneln Bootstrap program
– code stored in ROM that is able to locate the kernel, load it into memory, and start its execution
– starting a computer by loading the kerneln Bootstrap program
– code stored in ROM that is able to locate the kernel, load it into memory, and start its execution
Saturday, July 4, 2009
4.) SYSTEM STRUCTURE
Simple Structure
>View the OS as a series of levels>Each level performs a related subset of functions
>Each level relies on the next lower level to perform more primitive functions
>This decomposes a problem into a number of more manageable subproblems
Layered Approach
The operating system is divided into a number of layers (levels), each built on top of lower layers. The bottom layer (layer 0), is the hardware; the highest (layer N) is the user interface.
Thursday, July 2, 2009
1.) SYSTEM COMPONENT
OPERATING SYSTEM PROCESS MANAGEMENT
-A process is a program in execution. A process needs certain resources: CPU time, memory (address space), files, and I/O devices, to accomplish its task.
The operating system is responsible for the following activities in connection with process management.
>Process creation and deletion.
>Process suspension and resumption.
>Provision of mechanisms for:
>Process synchronization
>Process communication
MAIN MEMORY MANAGEMENT
-Memory is a large array of words or bytes, each with its own address. It is a repository of instructions and data shared by the CPU and I/O devices. Main memory is a volatile storage device. It loses its contents in the case of system failure.
The operating system is responsible for the following activities in connections with memory management:
>Decide which processes to load when memory space becomes available.
>Allocate and deallocate memory space as needed. Keep track of which parts of memory are currently being used and by whom.
FILE MANAGEMENT
-A file is a collection of related information defined by its creator. Commonly, files represent programs (both source and object forms) and data.
The operating system is responsible for the following activities in connections with file management:
>File creation and deletion.
>Directory creation and deletion.
>Support of primitives for manipulating files and directories.
>Mapping files onto secondary storage.
>File backup on stable (nonvolatile) storage media.
>Files on floppy are inaccessible
>Ffiles on floppy are part of file hierarchy
I/O SYSTEM MANAGEMENT
-The I/O system consists of:
>A buffer-caching system
>A general device-driver interface
>Drivers for specific hardware devices
SECONDARY STORAGE MANAGEMENT
-Since main memory (primary storage) is volatile and too small to accommodate all data and programs permanently, the computer system must provide secondary storage to back up main memory.
Most modern computer systems use disks as the principle on-line storage medium, for both programs and data.
The operating system is responsible for the following activities in connection with disk management:
-->Free space management
-->Storage allocation
-->Disk scheduling
PROTETION SYSTEM
-Protection refers to a mechanism for controlling access by programs, processes, or users to both system and user resources.
The protection mechanism must:
>Distinguish between authorized and unauthorized usage.
>Specify the controls to be imposed.
>Provide a means of enforcement.
COMMAND-INTERPRETER
-Command-Interpreter reads commands from the user or from a file of commandsand executes them, usually by turning them into one or more systemcalls. It is usually not part of the kernel since the command interpreteris subject to changes.
The program that reads and interprets control statements is called variously:
>command-line interpreter
>shell (in UNIX)Its function is to get and execute the next command statement
-A process is a program in execution. A process needs certain resources: CPU time, memory (address space), files, and I/O devices, to accomplish its task.
The operating system is responsible for the following activities in connection with process management.
>Process creation and deletion.
>Process suspension and resumption.
>Provision of mechanisms for:
>Process synchronization
>Process communication
MAIN MEMORY MANAGEMENT
-Memory is a large array of words or bytes, each with its own address. It is a repository of instructions and data shared by the CPU and I/O devices. Main memory is a volatile storage device. It loses its contents in the case of system failure.
The operating system is responsible for the following activities in connections with memory management:
>Decide which processes to load when memory space becomes available.
>Allocate and deallocate memory space as needed. Keep track of which parts of memory are currently being used and by whom.
FILE MANAGEMENT
-A file is a collection of related information defined by its creator. Commonly, files represent programs (both source and object forms) and data.
The operating system is responsible for the following activities in connections with file management:
>File creation and deletion.
>Directory creation and deletion.
>Support of primitives for manipulating files and directories.
>Mapping files onto secondary storage.
>File backup on stable (nonvolatile) storage media.
>Files on floppy are inaccessible
>Ffiles on floppy are part of file hierarchy
I/O SYSTEM MANAGEMENT
-The I/O system consists of:
>A buffer-caching system
>A general device-driver interface
>Drivers for specific hardware devices
SECONDARY STORAGE MANAGEMENT
-Since main memory (primary storage) is volatile and too small to accommodate all data and programs permanently, the computer system must provide secondary storage to back up main memory.
Most modern computer systems use disks as the principle on-line storage medium, for both programs and data.
The operating system is responsible for the following activities in connection with disk management:
-->Free space management
-->Storage allocation
-->Disk scheduling
PROTETION SYSTEM
-Protection refers to a mechanism for controlling access by programs, processes, or users to both system and user resources.
The protection mechanism must:
>Distinguish between authorized and unauthorized usage.
>Specify the controls to be imposed.
>Provide a means of enforcement.
COMMAND-INTERPRETER
-Command-Interpreter reads commands from the user or from a file of commandsand executes them, usually by turning them into one or more systemcalls. It is usually not part of the kernel since the command interpreteris subject to changes.
The program that reads and interprets control statements is called variously:
>command-line interpreter
>shell (in UNIX)Its function is to get and execute the next command statement
3.) SYSTEM CALLS
- An operating system (O/S) is a program with two jobs: it manages the resources of the computer (peripherals, files, memory, etc.) and it manages all other programs running on the computer.
PROCESS CONTROL
-Process control is a statistics and engineering discipline that deals with architectures, mechanisms, and algorithms for controlling the output of a specific process. See also control theory.
For example, heating up the temperature in a room is a process that has the specific, desired outcome to reach and maintain a defined temperature (e.g. 20°C), kept constant over time. Here, the temperature is the controlled variable. At the same time, it is the input variable since it is measured by a thermometer and used to decide whether to heat or not to heat. The desired temperature (20°C) is the setpoint. The state of the heater (e.g. the setting of the valve allowing hot water to flow through it) is called the manipulated variable since it is subject to control actions.
A commonly used control device called a programmable logic controller, or a PLC, is used to read a set of digital and analog inputs, apply a set of logic statements, and generate a set of analog and digital outputs. Using the example in the previous paragraph, the room temperature would be an input to the PLC. The logical statements would compare the setpoint to the input temperature and determine whether more or less heating was necessary to keep the temperature constant. A PLC output would then either open or close the hot water valve, an incremental amount, depending on whether more or less hot water was needed. Larger more complex systems can be controlled by a Distributed Control System (DCS) or SCADA system.
FILE MANAGEMENT
-The term computer file management refers to the manipulation of [document]s and [data] in [Computer filefile]s on a [computer]].
Specifically, one may create a new file or edit an existing file and save it; open or load a pre-existing file into memory; or close a file without saving it. Additionally, one may group related files in directories. These tasks are accomplished in different ways in different operating systems and depend on the user interface design and, to some extent, the storage medium being used.
DEVICE MANAGEMENT
-Device Management is a set of technologies, protocols and standards used to allow the remote management of mobile devices, often involving updates of firmware over the air (FOTA). The network operator, handset OEM or in some cases even the end-user (usually via a web portal) can use Device Management, also known as Mobile Device Management, or MDM, to update the handset firmware/OS, install applications and fix bugs, all over the air. Thus, large numbers of devices can be managed with single commands and the end-user is freed from the requirement to take the phone to a shop or service center to refresh or update.
For companies, a Device Management system means better control and safety as well as increased efficiency, decreasing the possibility for device downtime. As the number of smart devices increases in many companies today, there is a demand for managing, controlling and updating these devices in an effective way. As mobile devices have become true computers over the years, they also force organizations to manage them properly. Without proper management and security policies, mobile devices pose threat to security: they contain lots of information, while they may easily get into wrong hands. Normally an employee would need to visit the IT / Telecom department in order to do an update on the device. With a Device Management system, that is no longer the issue. Updates can easily be done "over the air". The content on a lost or stolen device can also easily be removed by "wipe" operations. In that way sensitive documents on a lost or a stolen device do not arrive in the hands of others.
INFORMATION MAINTENANCE
-A one or two-year program open to juniors and seniors who want to work with the repair and maintenance of computers OR the networking of computers. Repair and maintenance: This class will prepare students with competencies essential for repairing and maintaining computer hardware and operating systems, as well as simple network concepts. Qualified students may enroll in coursework that may lead to certification as an A+ Computer Technician. Networking: Second year students may enroll in Cisco Academy or sample the high tech areas of computer usage that include internet concepts and applications and computer hardware and electronic interfacing projects. Qualified students may enroll in coursework that may lead to a Cisco Certified Network Associate (CCNA) or Network+ Certification.
PROCESS CONTROL
-Process control is a statistics and engineering discipline that deals with architectures, mechanisms, and algorithms for controlling the output of a specific process. See also control theory.
For example, heating up the temperature in a room is a process that has the specific, desired outcome to reach and maintain a defined temperature (e.g. 20°C), kept constant over time. Here, the temperature is the controlled variable. At the same time, it is the input variable since it is measured by a thermometer and used to decide whether to heat or not to heat. The desired temperature (20°C) is the setpoint. The state of the heater (e.g. the setting of the valve allowing hot water to flow through it) is called the manipulated variable since it is subject to control actions.
A commonly used control device called a programmable logic controller, or a PLC, is used to read a set of digital and analog inputs, apply a set of logic statements, and generate a set of analog and digital outputs. Using the example in the previous paragraph, the room temperature would be an input to the PLC. The logical statements would compare the setpoint to the input temperature and determine whether more or less heating was necessary to keep the temperature constant. A PLC output would then either open or close the hot water valve, an incremental amount, depending on whether more or less hot water was needed. Larger more complex systems can be controlled by a Distributed Control System (DCS) or SCADA system.
FILE MANAGEMENT
-The term computer file management refers to the manipulation of [document]s and [data] in [Computer filefile]s on a [computer]].
Specifically, one may create a new file or edit an existing file and save it; open or load a pre-existing file into memory; or close a file without saving it. Additionally, one may group related files in directories. These tasks are accomplished in different ways in different operating systems and depend on the user interface design and, to some extent, the storage medium being used.
DEVICE MANAGEMENT
-Device Management is a set of technologies, protocols and standards used to allow the remote management of mobile devices, often involving updates of firmware over the air (FOTA). The network operator, handset OEM or in some cases even the end-user (usually via a web portal) can use Device Management, also known as Mobile Device Management, or MDM, to update the handset firmware/OS, install applications and fix bugs, all over the air. Thus, large numbers of devices can be managed with single commands and the end-user is freed from the requirement to take the phone to a shop or service center to refresh or update.
For companies, a Device Management system means better control and safety as well as increased efficiency, decreasing the possibility for device downtime. As the number of smart devices increases in many companies today, there is a demand for managing, controlling and updating these devices in an effective way. As mobile devices have become true computers over the years, they also force organizations to manage them properly. Without proper management and security policies, mobile devices pose threat to security: they contain lots of information, while they may easily get into wrong hands. Normally an employee would need to visit the IT / Telecom department in order to do an update on the device. With a Device Management system, that is no longer the issue. Updates can easily be done "over the air". The content on a lost or stolen device can also easily be removed by "wipe" operations. In that way sensitive documents on a lost or a stolen device do not arrive in the hands of others.
INFORMATION MAINTENANCE
-A one or two-year program open to juniors and seniors who want to work with the repair and maintenance of computers OR the networking of computers. Repair and maintenance: This class will prepare students with competencies essential for repairing and maintaining computer hardware and operating systems, as well as simple network concepts. Qualified students may enroll in coursework that may lead to certification as an A+ Computer Technician. Networking: Second year students may enroll in Cisco Academy or sample the high tech areas of computer usage that include internet concepts and applications and computer hardware and electronic interfacing projects. Qualified students may enroll in coursework that may lead to a Cisco Certified Network Associate (CCNA) or Network+ Certification.
2.) OPERATING SYSTEM SERVICES
-An operating system (commonly abbreviated to either OS or O/S) is an interface between hardware and user; an OS is responsible for the management and coordination of activities and the sharing of the resources of the computer. The operating system acts as a host for computing applications that are run on the machine. As a host, one of the purposes of an operating system is to handle the details of the operation of the hardware. This relieves application programs from having to manage these details and makes it easier to write applications. Almost all computers (including handheld computers, desktop computers, supercomputers, video game consoles) as well as some robots, domestic appliances (dishwashers, washing machines), and portable media players use an operating system of some type. [1] Some of the oldest models may however use an embedded operating system, that may be contained on a compact disk or other data storage device.
Operating systems offer a number of services to application programs and users. Applications access these services through application programming interfaces (APIs) or system calls. By invoking these interfaces, the application can request a service from the operating system, pass parameters, and receive the results of the operation. Users may also interact with the operating system with some kind of software user interface (UI) like typing commands by using command line interface (CLI) or using a graphical user interface (GUI, commonly pronounced “gooey”). For hand-held and desktop computers, the user interface is generally considered part of the operating system. On large multi-user systems like Unix and Unix-like systems, the user interface is generally implemented as an application program that runs outside the operating system. (Whether the user interface should be included as part of the operating system is a point of contention.)
Operating systems offer a number of services to application programs and users. Applications access these services through application programming interfaces (APIs) or system calls. By invoking these interfaces, the application can request a service from the operating system, pass parameters, and receive the results of the operation. Users may also interact with the operating system with some kind of software user interface (UI) like typing commands by using command line interface (CLI) or using a graphical user interface (GUI, commonly pronounced “gooey”). For hand-held and desktop computers, the user interface is generally considered part of the operating system. On large multi-user systems like Unix and Unix-like systems, the user interface is generally implemented as an application program that runs outside the operating system. (Whether the user interface should be included as part of the operating system is a point of contention.)
Subscribe to:
Posts (Atom)